top of page
Search
Top 5 Cybersecurity Threats Businesses Face in 2025
In today’s digital-first world, cybersecurity isn’t a luxury—it’s a necessity. With evolving threats and sophisticated attack strategies,...

Jeremy Druin
Jan 20, 20252 min read
How to Secure Your WordPress Site
WordPress powers over 40% of all websites on the internet, making it one of the most popular content management systems (CMS) available....

Jeremy Druin
Jan 20, 20253 min read
Securing Your Small Business on a Budget
In today’s digital world, small businesses are increasingly becoming targets for cybercriminals. Many small business owners believe they...

Jeremy Druin
Jan 20, 20254 min read
API Security: The Critical Role of Input Validation
As organizations increasingly rely on Application Programming Interfaces (APIs) to deliver seamless digital experiences, securing these...

Jeremy Druin
Jan 13, 20253 min read
API Security: Protecting Your Business
As organizations increasingly rely on Application Programming Interfaces (APIs) to deliver seamless digital experiences, API security has...

Jeremy Druin
Jan 12, 20253 min read
The Truth About Password Security: Why Length Beats Complexity
When it comes to password security, many organizations still follow outdated practices that create frustration for users without truly...

Jeremy Druin
Jan 12, 20253 min read


How to Check HTTP Headers
HTTP response headers can impact the user experience and the security of the web or mobile application. Server administrators can...

Jeremy Druin
Apr 2, 20211 min read


Retiring Obsolete JavaScript Libraries
One of the most over-looked issues in web applications is vulnerabilities in someone else's code; 3rd-party JavaScript libraries. Vendors...

Jeremy Druin
Mar 22, 20211 min read


What is Content Security Policy?
Content Security Policy (CSP) is a security framework built into the browser. CSP allows the browser to block content from sources other...

Jeremy Druin
Mar 6, 20211 min read
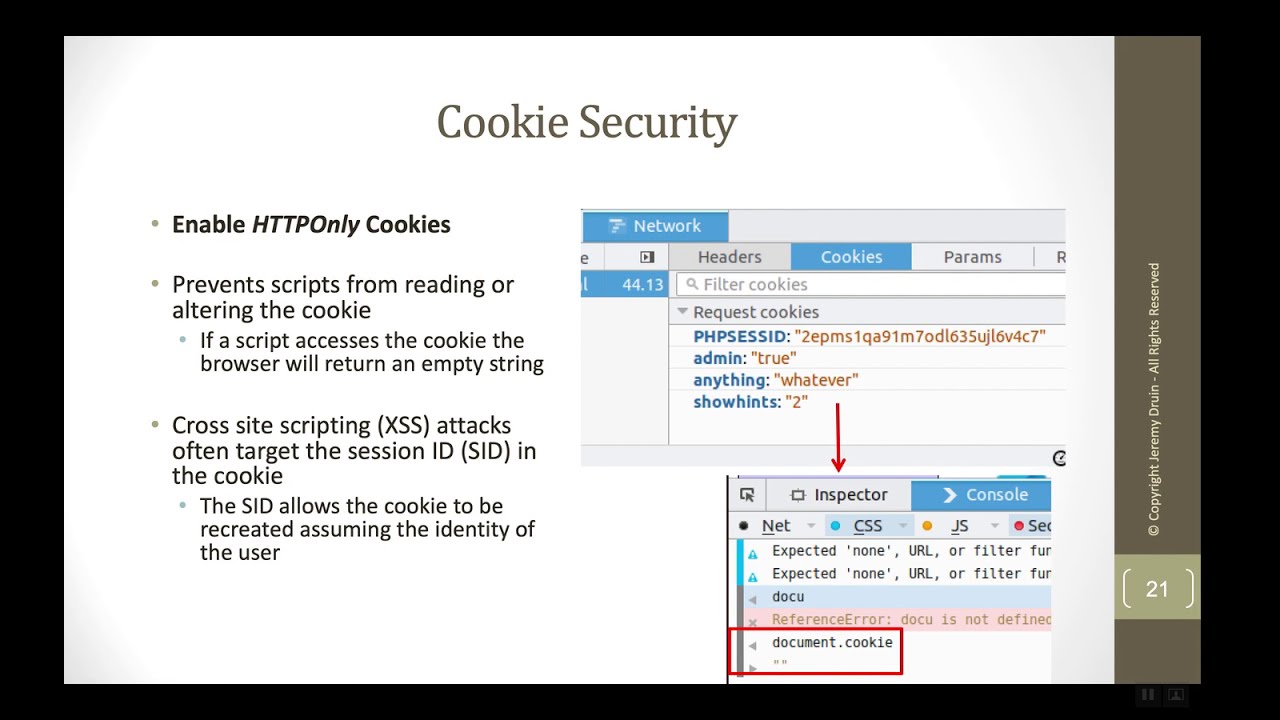

Yum! Secure Cookies
Cookie security is an oxymoron. Cookies exist in the browser; an inherently insecure location. However, there are several best-practices...

Jeremy Druin
Mar 1, 20211 min read


How HTTP Headers impact Application Security (by Example)
Web server configuration can impact the security of the web site and underlying application. These headers can be confusing so it is not...

Jeremy Druin
Feb 25, 20211 min read


What is DevSecOps?
DevSecOps is a development methodolgy that enables rugged software with quality baked in from the start. A key component is security....

Jeremy Druin
Feb 24, 20211 min read


ZAPping Web Application Vulnerabilities
Vulnerability assessment is a great addition to development lifecycles. Vulnerabilities found early are easier and cheaper to fix plus...

Jeremy Druin
Feb 22, 20211 min read


Weak HTTPS Ciphers? There is an app for that
HTTPS connection depend on the underlying cryptopgraphic algorithms that are available to the web server. Also, the web server...

Jeremy Druin
Feb 22, 20211 min read


How Output Encoding Stops Cross-site Script (XSS) Attacks
Output encoding is a powerful defense against cross-site script (XSS) attacks. Output encoding clearly marks information in web pages as...

Jeremy Druin
Feb 21, 20211 min read


How Cross-Site Request Forgery (CSRF) Tokens Work
CSRF tokens allow applications to detect forged requests such as those created by malicious scripts. Watch this video to see how CSRF...

Jeremy Druin
Feb 21, 20211 min read


Security Mistakes Everyone Makes: Improving Personal, Mobile and Home Network Security - Part II
Looking for Part I? - Link: Security Mistakes Everyone Makes: Improving Personal, Mobile and Home Network Security - Part I I hope you...

Jeremy Druin
Jan 9, 20215 min read


Resources and Publications
Checklists Home Network Security Tips Password Security Tips Home router and Wi-Fi Security Tips Container Security Tips DevSecOps...

Jeremy Druin
Jan 7, 20211 min read


Security Mistakes Everyone Makes: Improving Personal, Mobile and Home Network Security - Part I
Perfection is unrealistic but making relatively easy changes can significantly improve the security of mobile devices and home networks....

Jeremy Druin
Jan 7, 20216 min read


Demystifying the HTTP Strict Transport Security (HSTS) Header
Ideally, web sites would run exclusively over HTTPS. In the future, we might find sites avoiding HTTP entirely using one of the following...

Jeremy Druin
Dec 13, 20204 min read
bottom of page
