top of page
Search


How to Check HTTP Headers
HTTP response headers can impact the user experience and the security of the web or mobile application. Server administrators can...

Jeremy Druin
Apr 2, 20211 min read


Retiring Obsolete JavaScript Libraries
One of the most over-looked issues in web applications is vulnerabilities in someone else's code; 3rd-party JavaScript libraries. Vendors...

Jeremy Druin
Mar 22, 20211 min read


What is Content Security Policy?
Content Security Policy (CSP) is a security framework built into the browser. CSP allows the browser to block content from sources other...

Jeremy Druin
Mar 6, 20211 min read
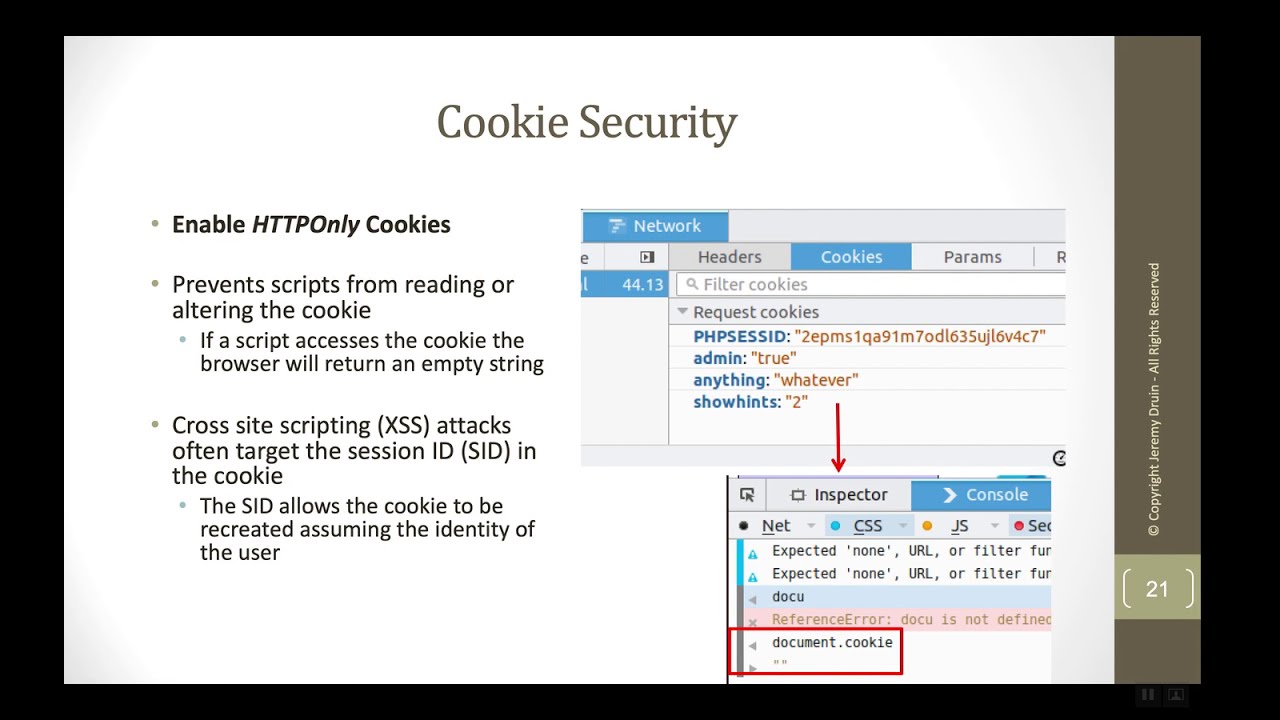

Yum! Secure Cookies
Cookie security is an oxymoron. Cookies exist in the browser; an inherently insecure location. However, there are several best-practices...

Jeremy Druin
Mar 1, 20211 min read


How HTTP Headers impact Application Security (by Example)
Web server configuration can impact the security of the web site and underlying application. These headers can be confusing so it is not...

Jeremy Druin
Feb 25, 20211 min read


What is DevSecOps?
DevSecOps is a development methodolgy that enables rugged software with quality baked in from the start. A key component is security....

Jeremy Druin
Feb 24, 20211 min read


ZAPping Web Application Vulnerabilities
Vulnerability assessment is a great addition to development lifecycles. Vulnerabilities found early are easier and cheaper to fix plus...

Jeremy Druin
Feb 22, 20211 min read


Weak HTTPS Ciphers? There is an app for that
HTTPS connection depend on the underlying cryptopgraphic algorithms that are available to the web server. Also, the web server...

Jeremy Druin
Feb 22, 20211 min read


How Output Encoding Stops Cross-site Script (XSS) Attacks
Output encoding is a powerful defense against cross-site script (XSS) attacks. Output encoding clearly marks information in web pages as...

Jeremy Druin
Feb 21, 20211 min read


How Cross-Site Request Forgery (CSRF) Tokens Work
CSRF tokens allow applications to detect forged requests such as those created by malicious scripts. Watch this video to see how CSRF...

Jeremy Druin
Feb 21, 20211 min read


Demystifying the HTTP Strict Transport Security (HSTS) Header
Ideally, web sites would run exclusively over HTTPS. In the future, we might find sites avoiding HTTP entirely using one of the following...

Jeremy Druin
Dec 13, 20204 min read
bottom of page
